As a business owner (or the one reporting to the owner) you may have concerns about the business that keeps you up at night. Whether you do or not, your data security and the type of VPN protocol used should be at the top of that list. Some companies have a higher need for data security than others. That is easily seen by how they protect their devices physically. Do you have door access controls on your data closet for an audit trail or do you just have a key that is given to a select group of employees? Are you concerned about the location of your data – is it in the cloud, on premise, or both? Do you have a redundancy plan? How do you protect your data when it is sent between your site and a remote office? (Remember, if I take my laptop home and access the system, I’m now a remote office).
Taylored Systems understands that not all companies are the same and not all needs are the same. We pride ourselves on being the technology experts so you can sleep soundly at night.
So what do you need to think about to help us help you select the best VPN tunnel setup?
- Are others interested in your data?
- From where does your data need to be accessed?
- Can you compromise access speed for cost?
- How capable are those managing your data?
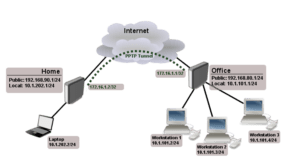
Data security is made up of many components but today we will focus on the accessibility of data between locations. In order to securely access data between sites it is highly recommended companies use a Virtual Private Network (VPN). VPN is a private and secure virtual connection between a user or device on your network and another user or device on another network. In order for a VPN to operate it needs to use a protocol to transmit the data. First let’s go through the common protocols.
PPTP (Point-to-Point Tunneling Protocol)
- VPN Encryption: 128-bit
- VPN Security: Basic encryption
- VPN Speed: Fast due to the low encryption rate
- Stability: Very good and stable on most Wi-Fi networks
- Compatibility: Most computer, tablet, and mobile operating systems come with PPTP
L2TP/IPsec (Layer 2 Tunneling Protocol over Internet Protocol Security)
- VPN Encryption: 256-bit
- VPN Security: Highest encryption. This protocol encapsulates and checks data integrity twice.
- VPN Speed: Requires more processing power because of the 2x encapsulation
- Stability: Stable on NAT-supported devices
- Compatibility: Like PPTP, it is included in most device operating systems
- SSTP (Secure Socket Tunneling Protocol)
- VPN Encryption: 256-bit
- VPN Security: Highest encryption. SSTP depends on cipher, but usually very strong AES
- VPN Speed: Speeds are fast and can bypass most firewalls
- Stability: This protocol is very stable and reliable.
- Compatibility: SSTP is primarily used in a Windows only environment, but is available for Linux, RouterOS and SEIL. Because it is a proprietary protocol owned by Microsoft, it cannot be independently audited for backdoors.
- OpenVPN
- VPN Encryption: 160-bit and 256-bit
- VPN Security: OpenVPN provides the highest encryption. OpenVPN authenticates the data with digital certificates and is the most secure VPN protocol.
- VPN Speed: This protocol has the best performance. Speeds are fast and are not susceptible to high latency connections or long distance transfers. Is your network connection stable and provide the right speeds?
- Stability: Most reliable and stable, even behind wireless routers, on non-reliable networks and on Wi-Fi.
- Compatibility: OpenVPN is supported by most desktop operating systems, Android mobile and tablet devices.
Different businesses have different needs and applications. It’s important you work with a trusted advisor before making any changes to your data or access systems. To be informed makes you a better business owner or manager. So what does all this mean to you? What is the best VPN protocol?
- PPTP is the least secure. Even though it was created by Microsoft, they don’t even use this protocol. Also, for any business worried about Big Brother, the NSA has been able to compromise this protocol; therefore, it is widely recommended to avoid this protocol. As easy as it is to set up and implement, it is a case of “too good to be true.”
- L2TP/IPsec is a good VPN solution for non-critical use; however, this protocol, like PPTP, has been compromised as well. So access of your data by prying eyes could be inevitable. With that being said, for a quick VPN setup without the need to install extra software, L2TP/IPsec remains useful, particularly for mobile devices. Is this something you’re going to implement yourself or use an expert? If implementing yourself, this may be the solution for you.
- Across many areas of the IT world, OpenVPN is easily the best all-around VPN solution. One downside could be the need for third party software on all platforms; however, the benefits easily make this a preferred recommendation. It is reliable, fast, and (most importantly) secure, although it usually needs a bit more setting up than the other protocols. Because of this additional VPN configuration, we highly recommend partnering with an IT provider to provide assistance.
- SSTP does offer most of the advantages of OpenVPN; however, it is mostly limited to a Windows environment. This means that it is better integrated into the OS, but is typically poorly supported by other VPN solutions.
With all this info you are now informed. You will have the knowledge and info to talk to your provider about what may be right for your business. Data is important. We never want to compromise security for ease of use or costs. If you do not feel you can do this yourself or if you would like to understand more about VPN capabilities and how your business can benefit, please reach out to a Taylored Systems representative and we will be happy to assist.


 PPTP (Point-to-Point Tunneling Protocol)
PPTP (Point-to-Point Tunneling Protocol)